
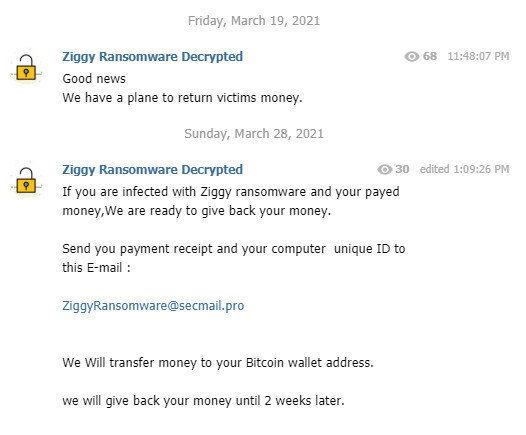
After recently announcing the end of the operation, the administrator of Ziggy ransomware is now stating that they will also give the money back.
It appears that this is a planned move since the admin shared the "good news" a little over a week ago, but gave no details.
Shutdown followed by money-back move
Ziggy ransomware shut down in early February. In a short announcement, the administrator of the operation said that they were “sad” about what they did and that they “decided to publish all decryption keys.”
They followed through the next day, on February 7, offering an SQL file with 922 decryption keys that victims could use to unlock their files.
The admin also made available a decryption tool to make the process easier, along with the source code for a decryptor that does not need an internet connection to work.
On March 19, the Ziggy ransomware administrator said that they also wanted to return the money to the victims that paid the ransom. Today, after a week of silence, the admin said that they were ready to revert payments.
Victims should contact the admin at a given email address (ziggyransomware@secmail.pro) with the proof of their payment in bitcoin and the computer ID, and the money would be returned to the victim’s bitcoin wallet in about two weeks.
Returning the ransom and making a profit
Ransomware victims get a ransom note with instructions on how to contact cybercriminals to negotiate a payment. Typically, the payment is negotiated in fiat but paid in Bitcoin.
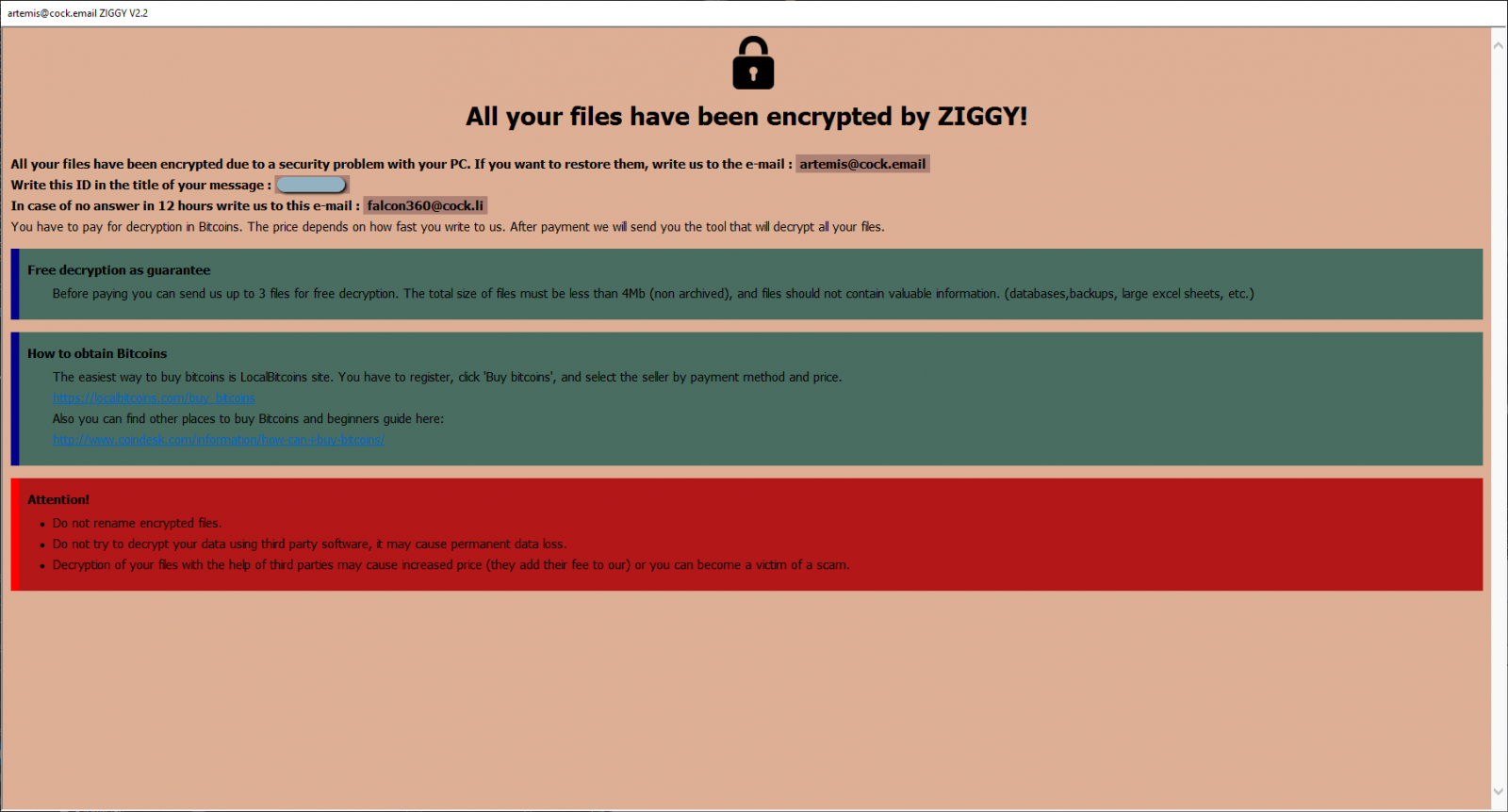
Speaking to BleepingComputer, the administrator of Ziggy ransomware said that the refund will be in Bitcoin at the value on payment day.
Bitcoin price has been on ascending route for the past three months, and its price at the moment of writing is close to $55,000.
On the day Ziggy ransomware decryption keys became public, Bitcoin price was around $39,000. Five days before the admin announced that they would return the money, Bitcoin spiked above $61,000. Given the price difference, the admin makes a profit at the current Bitcoin price.
The Ziggy ransomware administrator told BleepingComputer that they lived in a “third-world country” and that their motivation for creating the locker was financial. They confirmed to us that the recent actions are driven by fear of law enforcement getting them. Recent activity that disrupted much larger operations like Emotet and Netwalker ransomware likely weighed a lot towards this decision.
The admin also claims that they had to sell their house to be able to refund Ziggy ransomware victims and that they plan to switch sides and become a ransomware hunter after returning the money.
Update [March 29, 11:14 EST]: Article updated with information from the administrator of Ziggy ransomware.



Comments
cjgiam - 3 years ago
Not bad, but don't paint them as heroes. They look like nice people while still making anywhere from 42% to 57% profit.
The victims get back the extorted amount but still have lost possibly thousands in productivity & lost time, even if current backups were available
KeiFeR123 - 3 years ago
Exactly. Being a hunter does not necessarily meant the service will be free.
Paperclip - 3 years ago
Must have taken a lot if they need a plane to return victims money...
meeeezo - 3 years ago
They may also offer to give the victims free tickets for the cinemas.
what is that???
is it real in 2021?